Serious fears of privacy with the participation of over 40,000 security cameras have been revealed Bitsight Bitsight company. According to the company’s tracking research department, these cameras are live video broadcasts, which are fully exposed to the Internet-what means that you can access without the need for authentication, encryption and even a basic password. In most cases, a person can access the material from these exposed cameras in real time, knowing their IP address.
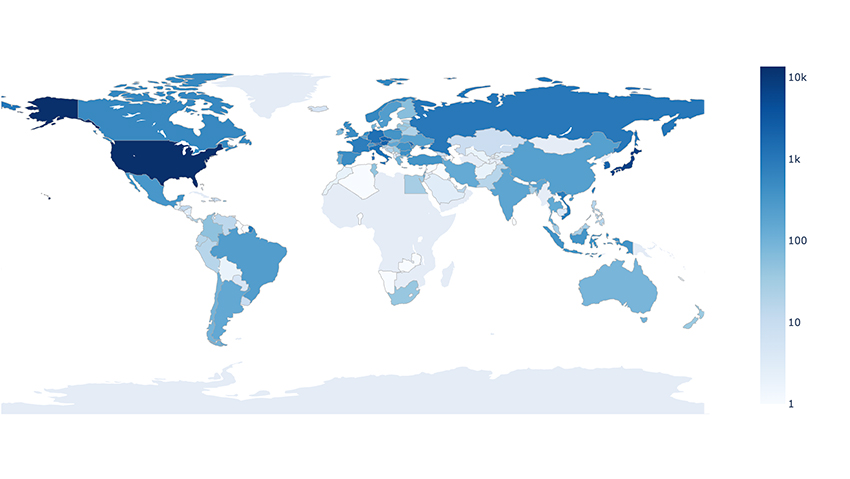
Initially Bitsight marked the problem in 2023But recent studies suggest that the situation “has not improved.” According to the latest research, these sensitive cameras are not narrow to one region or industry. The United States has nearly 14,000 cameras, which are potentially exposed, with countries such as California, Texas, Georgia and New York have the highest number. Then Japan is on the list, with 7,000 exposed cameras, followed by Austria, Czech and South Korea, each of which has nearly 2,000 sensitive devices.
It is true that not every camera connected to the internet is a reason for concern, and some live broadcasts are deliberately presented scenes, such as a beach or bird house, public viewing. However, some of these sensitive cameras were found in more private environments – including residential configurations monitoring doors, courtyards and even salons.
Cameras were also found in office spaces, factories and public transport systems. Bitsight researchers were able to observe sensitive spaces, monitor pedestrian traffic, and in some cases even see the details written on the boards – all in real time. It is said that most of the exposed devices employ HTTP, while the rest are sent via RTSP (real -time streaming protocol), which is a joint protocol of controlling and managing stream media by the IP networks.
In addition to increasing the fears of privacy and supervision, these exposed devices are earnest safety threats. Information collected by the Bitsight Cybernetic Intelligence Team suggest that users openly discuss channels on obscure internet forums where users provide tools and techniques to get unauthorized access, and even sell access to unsecured video streams.
Users and organizations are recommended twice to check how their cameras are configured: turn off access to remote access, if it is not in employ, update the latest firmware and make sure that the device is protected behind the dam or connected to a unthreatening network. A basic way to check if the camera is exposed or not is access to it outside the home network. If you can display the camera channel without logging in to a unthreatening application or via VPN (virtual private network), it is probably open to everyone on the Internet. In addition, any default users and password names should be mentioned, because many camera devices send the default confirmation set that are basic to break.
Follow Tom’s equipment in Google News To get current messages, analysis and reviews in your channels. Click the Fight button.